Technical functionality of a Blockchain
This section will give you an advanced understanding of Blockchain in a financial environment. However, after studying this section, you will not only be able to understand Blockchain for financial usage but for all kinds of usages. This section is for people who want to understand the theory of the technical implementation of Blockchain technology and it will also topic the basics of cryptography. I recommend you to read the article on Blockchain in the Beginners section first, before reading this one. The beginner's article will give you a basic understanding of what this article builds on. It is to say, that this article is oriented on the proof of Work mechanism to achieve consensus.
Key takeaways
-
The signature of a transaction verifies the sender's identity
-
Asymmetric encryption is used to sign a transaction
-
For encryption, a public and a private key is required
-
The private key should only be known by the owner
-
Any manipulation on the Blockchain will be visible to the peers
-
A wallet is a keychain that contains a public and a private key
What does a block look like?
In the beginner's article on Blockchain, I explained to you the three-step process for data to be saved in a Blockchain:
-
-
Data are packed into blocks
-
Blocks are encoded
-
Blocks are attached one after another
Here we will have a closer look at how data is packed into blocks, how the blocks are encoded, and how the blocks are attached one after another in a financial environment. The graphic below shows the elementary components a block needs to have.

Every block has an ongoing number and a nonce. Nonce is the short form of 'number once' and it is part of the cryptography puzzle every node is competing to solve first to qualify for adding a new block to the blockchain and getting rewarded for it. Normally, every block has data that has to be transmitted. In our financial context, the data contains transactions but it can contain all kinds of information. In this case, our transactions have several units that are transmitted (for example Bitcoin). It also has a sender of the units and it has a receiver. In the beginner's section, I explained to you, that every block is pointing to its previous one and that is how a 'chain' is created. Lastly, every block has a hash value. I will explain to you later what a hash value is. For now, it's important to know, that the hash value is like the nonce, part of the cryptographic puzzle that is to solve to attach a new block.
What is a hash function?
A hash function is a way to encrypt data. A hash function has two major characteristics: It always encrypts data to a fixed length and the encryption only works asymmetric. That means that you can take data, and put it into a hash function and the hash function will output a sequence of numbers and letters. This sequence has always the same amount of digits, no matter what the input is. What makes a hash function special is, that the same input will always generate the same output, but it is not possible to derive the input, given the output. That's why it is asymmetric. Imagine you are choosing a password for your online banking account. How can the system know that the correct password was typed in without actually saving the real password in their database? The answer is, that the system doesn't safe the real password. The password you chose is put into a hash function and only the output is stored in the systems database. The input (the real password) stays unknown and it can't be derived from the output. But if the right password is typed in, it will match the output that is saved in the system.
There are three characteristics you should remember on hash functions:
-
A hash function takes data and encrypts it to a fixed lengths of numbers and letters
-
The input cannot be derived from the output
-
The same input will always generate the same output
How are the blocks connected and what is mining?
Now that we know what a hash function is and what it does, let's have a look at the cryptography puzzle that every miner tries to solve. We learned, that every block has a unique hash function and every block (except the genesis block) contains the hash function of the previous block. The hash function of each block is created out of three components: the Block number, the nonce, the 'message' or in our case the transaction data, and the hash value of the previous block. All this data together generates a unique hash value for each block. Even if one block has the same transactions as another block, the hash value will remain unique because the block number will always differ from another block.

If you have a close look at the hash values in the above graphic, you will realize, that every hash value starts with a certain amount of zeros in the beginning. This is not a coincidence but is part of the cryptographic puzzler every node has to solve. The arrangement of the characters in a hash value is random because as you remember, the input cannot be derived from the output. If it is required, that a hash function has to start with a certain amount of zeros at the beginning, and all the other parameters: Block number, transaction data, and the hash value of the previous block are given, then, the nonce is the only variable that can create a hash value with that characteristic. This is called the mining process. Every node is trying to find a nonce that will produce a hash value which produces an output with a special characteristic. The first miner who found the right nonce, is allowed to add the next block to the blockchain. Now as you can imagine, before the right nonce is found, multiple constellations have to be tried out to find a right one.
What makes Blockchain a secure network?
As you remember, a main characteristic of Blockchain technology is, that Data is stored in a decentralized manner. It is also called a Peer-to-Peer network (P2P) because every participant has a copy of the blockchain on his computer. In the below graphic, you have an example of what a Peer-to-Peer network of four participants could look like. Every Peer A to D has the same copy of the blockchain on his computer.

Let's imagine now that one peer tries to manipulate a transaction and see what it would look like.

In the above example, Peer B tried to manipulate a transaction on Block #501. Because the hash value of every block takes the transaction data as input, a manipulated transaction will lead to a different hash value of the manipulated block. Not only will the manipulated transaction impact the hash value block #501, but it will also impact all blocks that are coming after. Peer B could re-mine block #501 and all that follows, but in fact, the manipulation would not be validated by the network. To execute a manipulation of a blockchain, the manipulator has to re-mine the manipulated block and all the blocks that are following. Moreover, the manipulator has to manipulate at least 51% of the copies of the peers to make the manipulation valid.
Asymmetric encryption and digital signature
Sending money through the use of Blockchain is like writing a check and going to a Bank to cash in. Imagine someone writes you a check for 100$ and you you go to a bank to cash in the 100$. What's important for the bank is that the check is signed by the financier. And doesn't matter how many people have seen the check before, what important is that the check is signed by the financier so the bank can be sure, that the money can be withdrawn from the debtor account and be deposited in the receiver's bank account. The signature allows the bank to make sure, that the transaction is legit. A signature of another person that is not the financier would not lead to any transaction. It would be of no value. The same principle applies to digital decentralized money transfers. The network needs to be sure, that the debited bank account is verified by the owner itself. Therefore a signature is required. But how can a signature can be realized digital, if everything can be copied and pasted? The answer is asymmetric encryption.
Asymmetric encryption allows the verification of a transaction. It ensures, that the wallet that is charged, is proofed by the owner of the wallet. The name 'wallet' suggest, that money is stored in it. In fact, a wallet can be imagined better as a keychain. All it does is to provide two keys. One public key that is accessible to everyone and one private key, that only the owner of the wallet should should own and nobody else. The actual balance of a person who holds cryptocurrencies is stored on the Blockchain and is visible to everyone. Of course, it is only visible through the pseudonym of the public key.
A private key can be selected as desired but it should be selected carefully like a password. Think of it, whoever knows the private keys of a wallet has access to the coins. After the private key is selected the public key can be generated through a hash function. The public key can be visible for everyone because as we already know, the private key can't be derived from the public key.

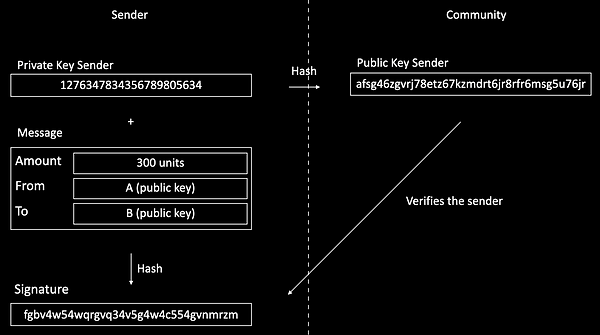
The next step is to make a transaction and sign the transaction to verify the sender. Therefore we take a closer look at how the transaction could look on a block. Let's take a transaction of 300 units of a coin as an example that has to be transferred from A to B. Therefore, the amount (300 units), the public key of the sender, and the public key of the receiver are required.

To sign the transaction, the private key of the sender is required. The signature is another hash value that is created from the transaction data plus the private key of the sender.

Now that the signature is created with the help of the private key of the sender, everyone can verify with the help of the sender's public key which is accessible to everyone, if the transaction is valid or not. If the signature is compatible with the public key from the sender, it is verified that whoever set up the transaction, had access to the sender's private key. Remember that the purpose of the signature is to verify the sender.
Conclusion
With the help of asymmetric encryption, digital transactions can be executed in a decentralized way. The graphics below can give you an idea of how a blockchain could look like. Every subsequent change on the blockchain will change the signature and the hash value of a block. The block can be re-mined, but the signature will remain false.

One block (exemplary)

A chain of blocks (exemplary)

A Peer-to-Peer network where every node has an exact copy of the Blockchain (exemplary)
If Peter wants to send 300 coins to Ronny, then Peter would put his and Ronnys public keys to place the transaction. For verification, Peter encrypts his transaction with the help of his private key which only he should know. After the signature is created and the transaction is on the blockchain, everyone can verify with Peters public key, that Peter has signed the transaction and it is valid. It is not possible, that Peter sends more coins than he actually owns, because all the coins he received in the past, can be tracked on the Blockchain.

If Sabine tries to manipulate the transaction and redirect the 300 coins to her wallet, she has to put her public key into the receiver's input box. After she did that, automatically the signature will change because the input values changed too. Every Peer in the network sees now, that the transaction was manipulated because the signature on the manipulated transaction differs from the signature on the other user copy of the Blockchain. The manipulation will stand out, because with a manipulated receivers address and a manipulated signature, the hash value of the block on which the transaction took place will also differ. This manipulation will be visible on all blocks that are following in the blockchain after the manipulated block. Sabine can re-mine the manipulated blocks to add them to the blockchain, but she can never correct the signature without knowing Peters private key. That makes the Blockchain a secure way to send data.

Cryptopedia101